AiTM Phishing Attacks
While phishing techniques vary in complexity, most attacks follow a similar structure. Understanding this structure helps identify where attacks begin, how they progress, and where defenses can be applied.
Below is a high-level overview of the typical stages involved in a phishing attack.
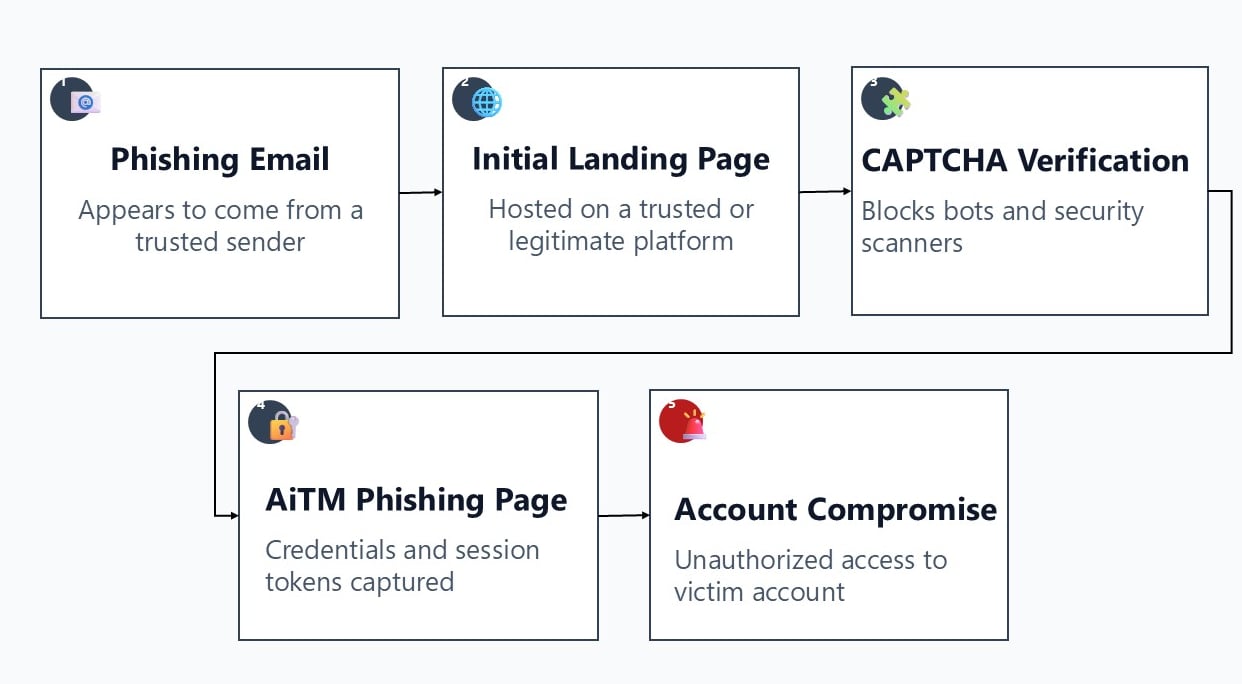
1. Phishing Email
The attack typically starts with a phishing email from a trusted contact who was compromised
2. Initial Landing Page
The phishing link directs the victim to an initial landing page, often hosted on a legitimate or widely trusted platform to avoid spam and security filtering.
3. CAPTCHA Verification Page
A CAPTCHA verification page is used to block automated scanners, bots, and email security tools from reaching the phishing infrastructure, while giving the interaction a sense of legitimacy.
4. AiTM Phishing Page
The victim is presented with the AiTM phishing page itself.
5. Account Compromise
Using the captured credentials, the attacker gains unauthorized access to the victim’s account.