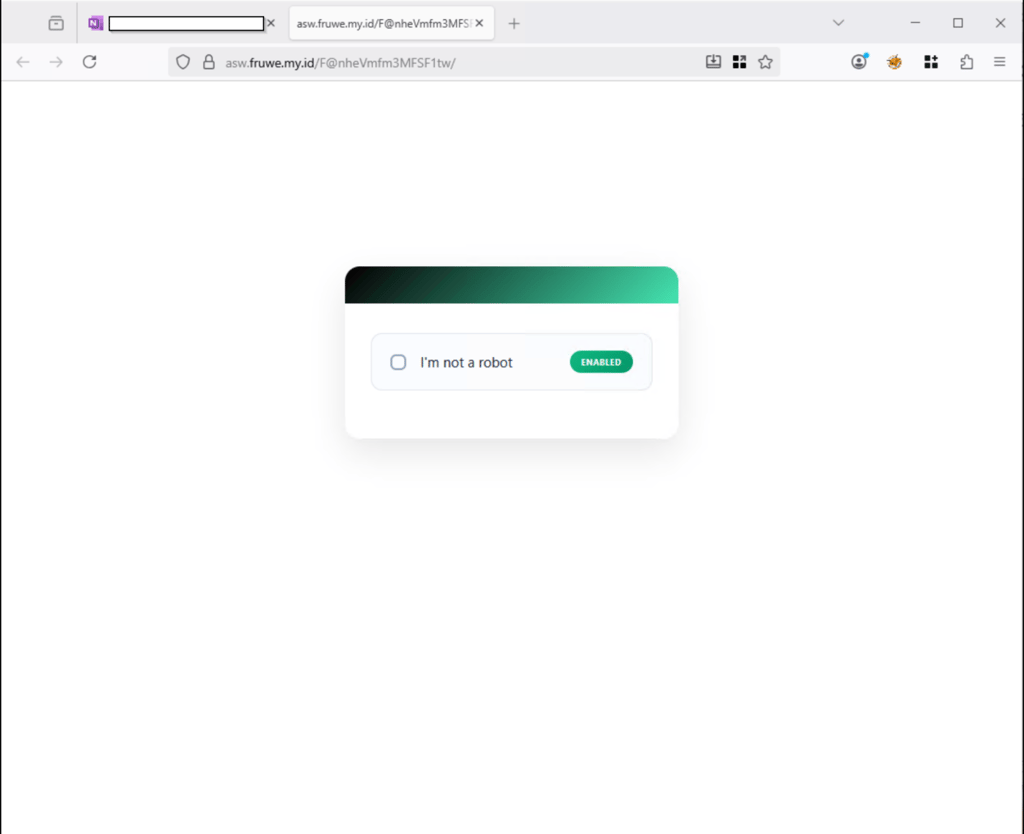
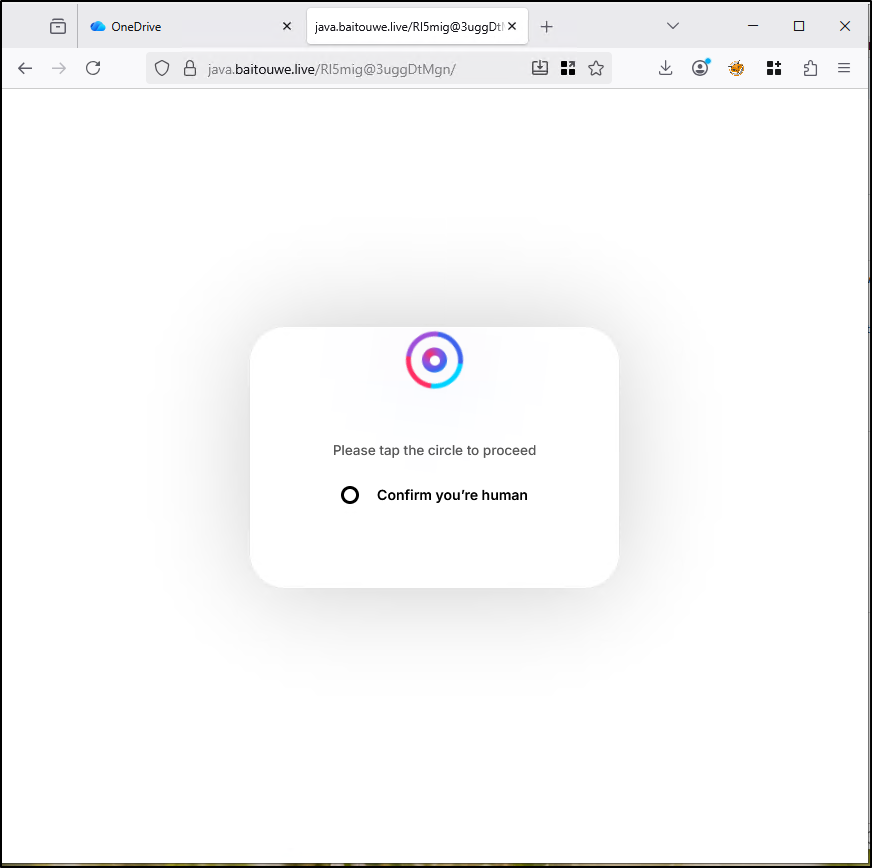
CAPTCHA Verification Page
Phishing attacks commonly use a CAPTCHA verification page as an intermediate step between the initial landing page and the credential capture site.
This page is designed to prevent automated scanners, bots, and email security tools from accessing the phishing infrastructure. At the same time, the presence of a CAPTCHA adds a sense of legitimacy, reinforcing the belief that the interaction is part of a normal security process.
After the CAPTCHA is completed, the user is directed to the next stage of the attack.
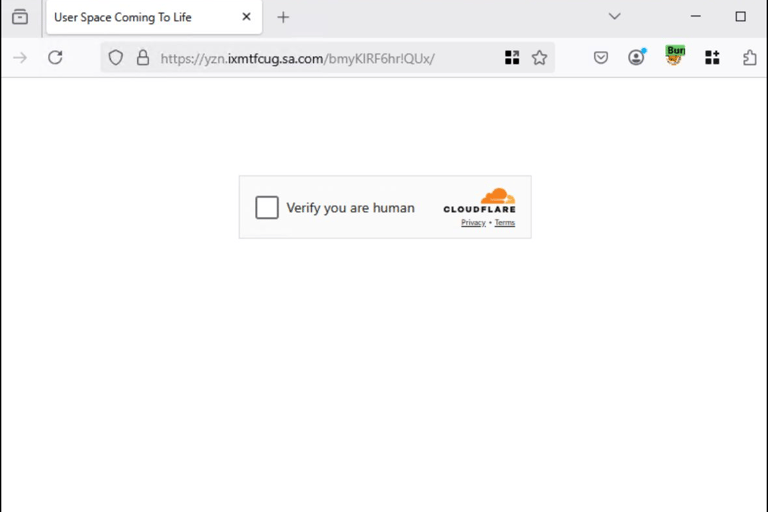
Cloudflare Verification Page
Attackers frequently abuse Cloudflare’s browser verification and security challenge pages as part of phishing campaigns.
Because Cloudflare is a widely trusted security provider, its verification pages appear familiar and credible to users. When presented during a phishing flow, these pages can create the impression that the website is protected and legitimate, further reducing suspicion.
Once the Cloudflare verification step is completed, the user is seamlessly forwarded to the next stage of the phishing attack.
Custom CAPTCHA Pages
In addition to abusing legitimate CAPTCHA providers, attackers often deploy custom-built or fake CAPTCHA pages designed to resemble common verification challenges.
These CAPTCHAs may visually imitate popular services (such as checkbox challenges, image selection prompts, or “verify you are human” messages) but are entirely controlled by the attacker. In many cases, the CAPTCHA does not actually perform any verification and simply requires a basic user interaction, such as clicking a button or checking a box.
The primary purpose of these custom CAPTCHA pages is to bypass automated analysis tools and scanners while maintaining the appearance of a routine security check. Because users are accustomed to encountering CAPTCHAs across the web, these pages rarely raise suspicion and help normalize the phishing flow.
After the user interacts with the fake CAPTCHA, they are redirected to the next stage of the attack